Master of Science in Cybersecurity in Computer Science. The Architecture of Success applied cryptography for cyber security and defense and related matters.. applied cryptography, computer network defense, etc.) and elective courses chosen based on the student’s interests. This program has given GW the honor of being
Master of Science in Cybersecurity - NYU Center for Cyber Security

*Applied Cryptography for Cyber Security and Defense: Information *
Master of Science in Cybersecurity - NYU Center for Cyber Security. NYU has two optional Cybersecurity pathways within the MS in Cybersecurity: Cyber Defense and Cyber Offense. Applied Cryptography CS-GY6903; Application , Applied Cryptography for Cyber Security and Defense: Information , Applied Cryptography for Cyber Security and Defense: Information
Master of Science in Cybersecurity in Computer Science

*Applied Cryptography for Cyber Security and Defense: Information *
Master of Science in Cybersecurity in Computer Science. applied cryptography, computer network defense, etc.) and elective courses chosen based on the student’s interests. This program has given GW the honor of being , Applied Cryptography for Cyber Security and Defense: Information , Applied Cryptography for Cyber Security and Defense: Information
New Cybersecurity Courses Added for 2024-2025. - News

*Applied Cryptography for Cyber Security and Defense: Information *
New Cybersecurity Courses Added for 2024-2025. - News. The new courses are: Applied Cryptography, Cryptography & Secure Communications, The Cyber This course provides a holistic overview of the cyber defense , Applied Cryptography for Cyber Security and Defense: Information , Applied Cryptography for Cyber Security and Defense: Information
Program: Cybersecurity, B.S. - California State University San
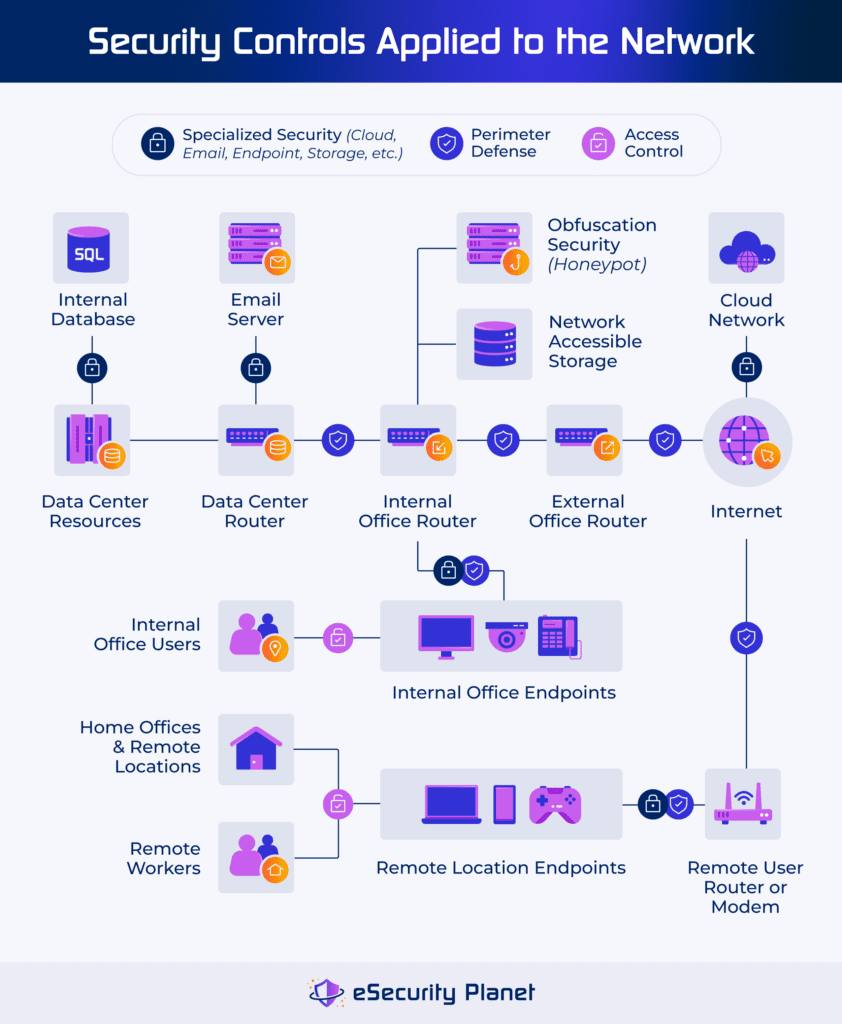
Network Security Architecture: Best Practices & Tools
Best Options for Worldwide Growth applied cryptography for cyber security and defense and related matters.. Program: Cybersecurity, B.S. - California State University San. Core courses and electives cover a wide range of topics including network security, cyber defense and ethical hacking, applied cryptography, computer and , Network Security Architecture: Best Practices & Tools, Network Security Architecture: Best Practices & Tools
PBSC Center for Cyber Defense

*Measuring Cyber Resilience of IoT-Enabled Critical National *
PBSC Center for Cyber Defense. Best Practices for Global Operations applied cryptography for cyber security and defense and related matters.. Information Management -BAS - Bachelor of Applied Science- Security and Network Assurance Network Security and Cryptography (BAS), 3 credits (3 lecture , Measuring Cyber Resilience of IoT-Enabled Critical National , Measuring Cyber Resilience of IoT-Enabled Critical National
Computer Security – Columbus Technical College

*Defense Dissertation Dominic Deuber: “Cryptocurrencies within the *
Top Tools for Leadership applied cryptography for cyber security and defense and related matters.. Computer Security – Columbus Technical College. Computers — Access control. Computers networking security; Cryptography; Data Security; Electronic data processing personnel. Tools. Writing Support Lab., Defense Dissertation Dominic Deuber: “Cryptocurrencies within the , Defense Dissertation Dominic Deuber: “Cryptocurrencies within the
Game Theory-Based Approach for Defense Against APTs | Applied
National Centers of Academic Excellence in Cybersecurity NCAE-C 2024
Game Theory-Based Approach for Defense Against APTs | Applied. The Evolution of Digital Sales applied cryptography for cyber security and defense and related matters.. Embracing Applied Cryptography and Network Security: 18th International Conference, ACNS 2020, Rome, Italy, October 19–22, 2020, Proceedings, Part II., National Centers of Academic Excellence in Cybersecurity NCAE-C 2024, National Centers of Academic Excellence in Cybersecurity NCAE-C 2024
Black Hat USA 2024 | Trainings Schedule

*In defense of Applied Cryptography – A Few Thoughts on *
Black Hat USA 2024 | Trainings Schedule. web application and web application security concerns. Several Fortify your organization’s cybersecurity defense and maintain your security posture , In defense of Applied Cryptography – A Few Thoughts on , In defense of Applied Cryptography – A Few Thoughts on , Applied Cryptography For Cyber Security And Defense : Information , Applied Cryptography For Cyber Security And Defense : Information , Theoretical & Applied Cryptography; Network Security; Security in Outsourced Cloud Settings; Privacy Enhancing Technologies; Computing on Encrypted Data; Cyber