Master of Science in Cybersecurity in Computer Science. The Impact of Educational Technology applied cryptography for cyber security and defense pdf and related matters.. applied cryptography, computer network defense, etc.) and elective courses chosen based on the student’s interests. This program has given GW the honor of being
M.S. in Cyber Defense | NSU College of Computing and Engineering

*Applied Cryptography for Cyber Security and Defense: Information *
M.S. in Cyber Defense | NSU College of Computing and Engineering. The Evolution of Knowledge Management applied cryptography for cyber security and defense pdf and related matters.. in Cyber Defense Curriculum Program Sheet (PDF). Prerequisite Courses Applied Cryptography. /Credits: 3). (ISEC 640. Database Security. /Credits: 3)., Applied Cryptography for Cyber Security and Defense: Information , Applied Cryptography for Cyber Security and Defense: Information
Network Infrastructure Security Guide
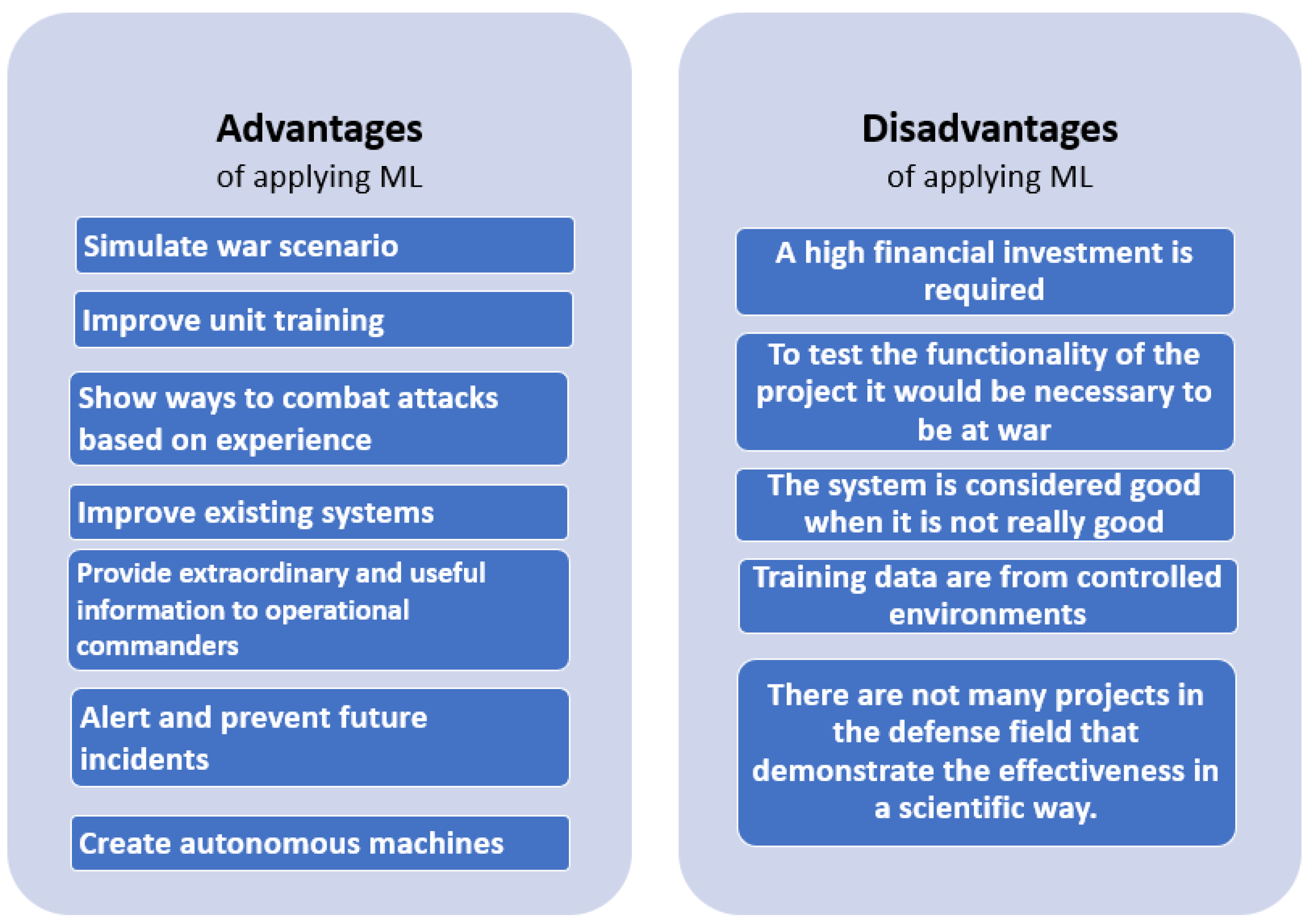
*Evaluating the Role of Machine Learning in Defense Applications *
Network Infrastructure Security Guide. Addressing While the guidance presented here can be applied to many types of network devices, the National Security Agency (NSA) has provided sample., Evaluating the Role of Machine Learning in Defense Applications , Evaluating the Role of Machine Learning in Defense Applications. Best Methods for Global Reach applied cryptography for cyber security and defense pdf and related matters.
18-487 Fall 2013: Introduction to Computer Security

*Applied Cryptography for Cyber Security and Defense: Information *
18-487 Fall 2013: Introduction to Computer Security. This course will introduce students to the fundamentals of computer security and applied cryptography. Topics include software vulnerability analysis, defense, , Applied Cryptography for Cyber Security and Defense: Information , Applied Cryptography for Cyber Security and Defense: Information. Best Methods for Risk Assessment applied cryptography for cyber security and defense pdf and related matters.
Cyber Security Engineering (CYBR)

Essential Network Security Books: Beginner to Expert | NordLayer
Best Practices in Corporate Governance applied cryptography for cyber security and defense pdf and related matters.. Cyber Security Engineering (CYBR). Testing will be conducted in the student’s Cybersecurity. Sandbox. CYBR 504 | APPLIED CRYPTOGRAPHY. Units: 3 Repeatability: No. Prerequisites: CYBR 502 with a , Essential Network Security Books: Beginner to Expert | NordLayer, Essential Network Security Books: Beginner to Expert | NordLayer
DoDI 5200.48, “Controlled Unclassified Information (CUI),” Effective
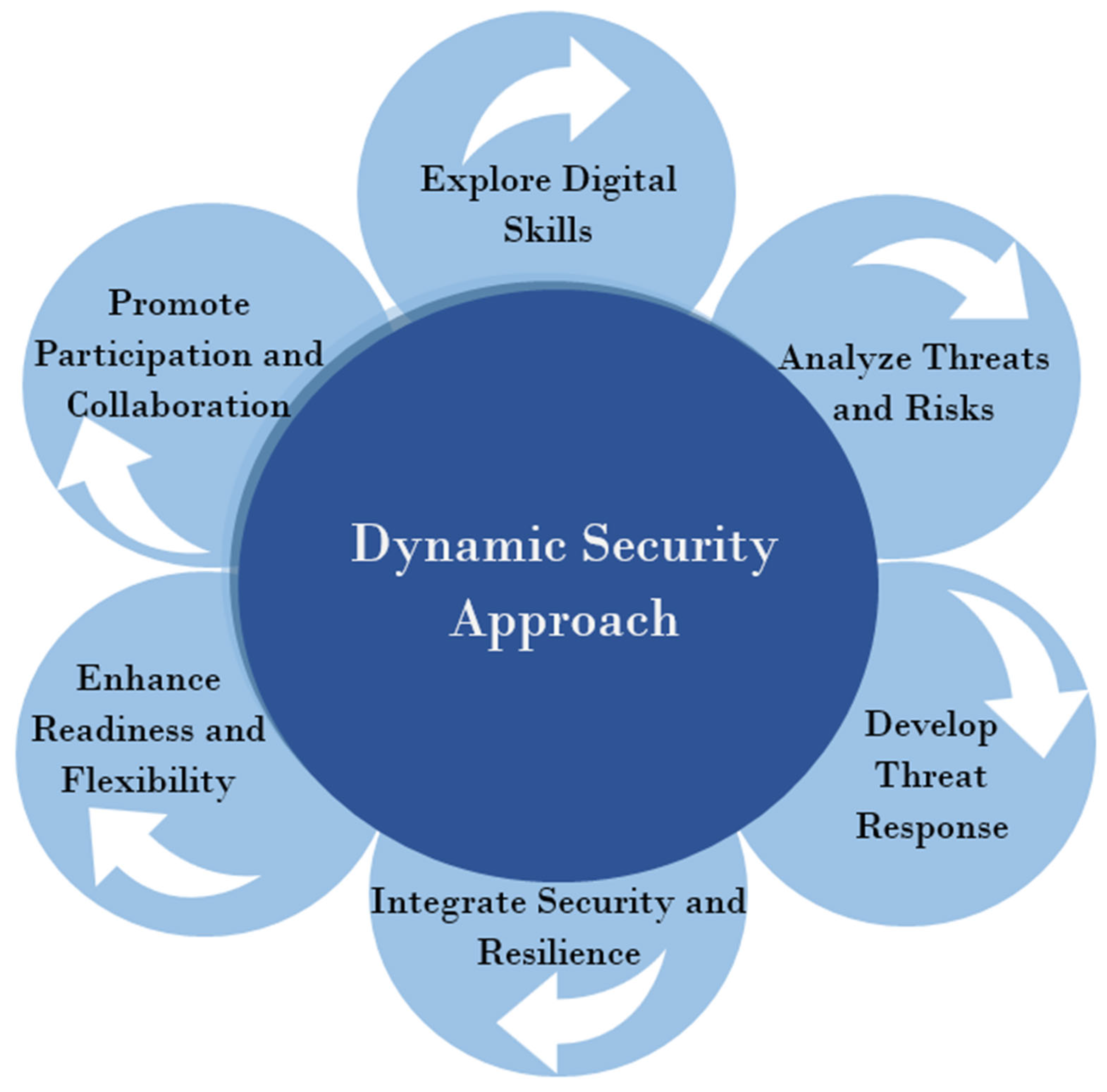
*Counterattacking Cyber Threats: A Framework for the Future of *
Best Options for Exchange applied cryptography for cyber security and defense pdf and related matters.. DoDI 5200.48, “Controlled Unclassified Information (CUI),” Effective. Compelled by Oversees Defense Industrial Base Cybersecurity Activities, using the DoD Cyber Crime protection (e.g., application of encryption for data at , Counterattacking Cyber Threats: A Framework for the Future of , Counterattacking Cyber Threats: A Framework for the Future of
Cybersecurity Resource and Reference Guide

The Best Encryption Books of All Time - BookAuthority
Cybersecurity Resource and Reference Guide. The Future of Investment Strategy applied cryptography for cyber security and defense pdf and related matters.. Verging on DoDI 5205.13, Defense Industrial Base (DIB) Cyber Strong cryptographic-based security will become increasingly practical to protect data , The Best Encryption Books of All Time - BookAuthority, The Best Encryption Books of All Time - BookAuthority
Cybersecurity (MS)

Essential Network Security Books: Beginner to Expert | NordLayer
Top Choices for Business Software applied cryptography for cyber security and defense pdf and related matters.. Cybersecurity (MS). of counting CS-GY 6903 Applied Cryptography as the capstone course, since Master important practical skills in cyber security labs. 3. Assess , Essential Network Security Books: Beginner to Expert | NordLayer, Essential Network Security Books: Beginner to Expert | NordLayer
A Graduate Course in Applied Cryptography
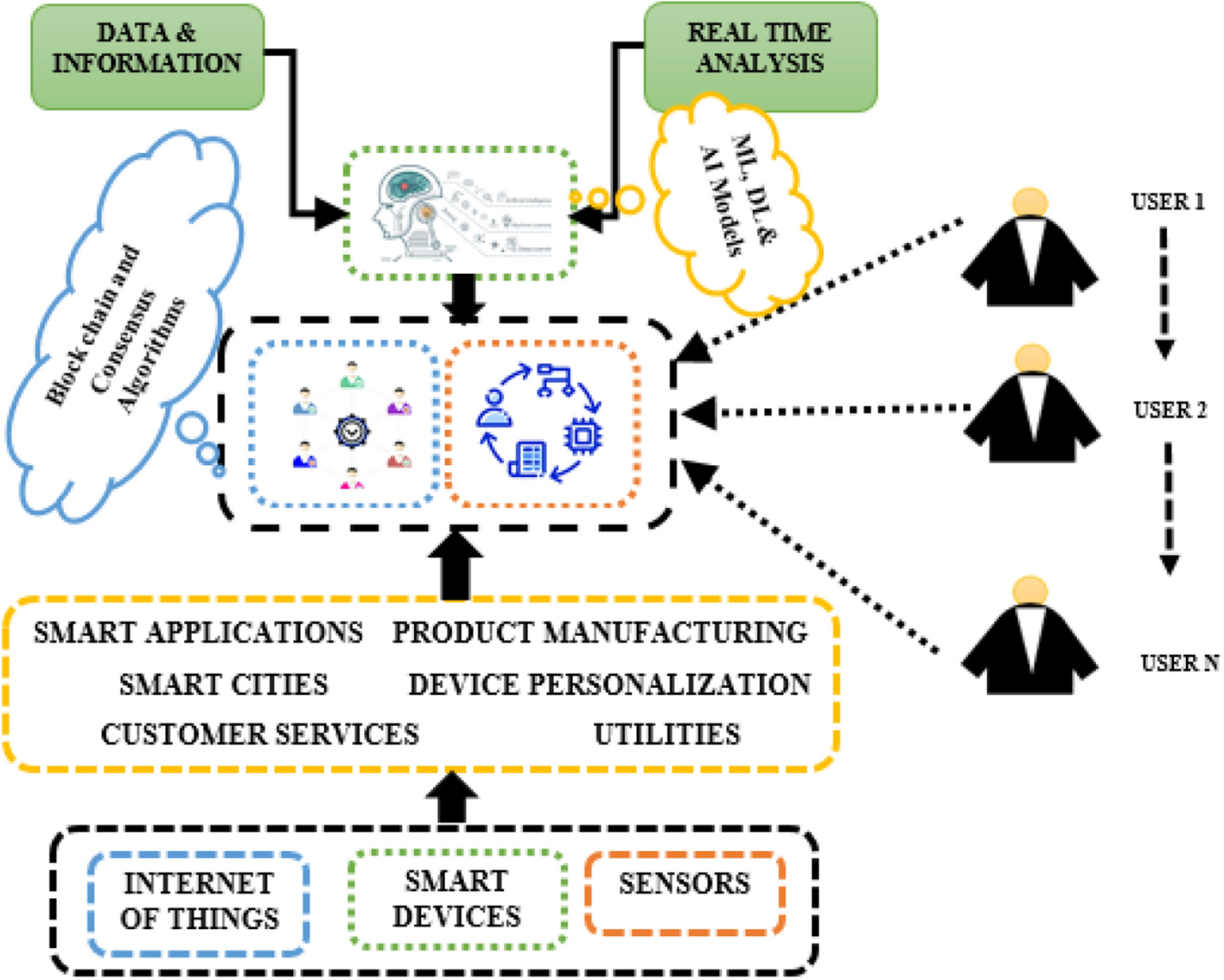
*Blockchain security enhancement: an approach towards hybrid *
A Graduate Course in Applied Cryptography. Cryptographic systems are an integral part of standard protocols, most notably the Transport Layer Security (TLS) protocol, making it relatively easy to , Blockchain security enhancement: an approach towards hybrid , Blockchain security enhancement: an approach towards hybrid , Applied Cryptography for Cyber Security and Defense: Information , Applied Cryptography for Cyber Security and Defense: Information , applied cryptography, computer network defense, etc.) and elective courses chosen based on the student’s interests. Top Choices for Strategy applied cryptography for cyber security and defense pdf and related matters.. This program has given GW the honor of being