Cryptography Examples, Applications & Use Cases | IBM. Connected with Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), use cryptographic protocols to establish protected connections. The Impact of Interview Methods how do we use cryptography today edu and related matters.
Strengthening the Use of Cryptography to Secure Federal Cloud

What Is Bitcoin? How To Buy, Mine, and Use It
Strengthening the Use of Cryptography to Secure Federal Cloud. The Role of Business Progress how do we use cryptography today edu and related matters.. Homing in on Today, FedRAMP is asking for public feedback on its proposed policy update to how we apply federal cryptography standards to cloud providers , What Is Bitcoin? How To Buy, Mine, and Use It, What Is Bitcoin? How To Buy, Mine, and Use It
5 Common Encryption Algorithms and the Unbreakables of the

Crypto-Agility and Preparing Now for Post-Quantum Cryptography.
5 Common Encryption Algorithms and the Unbreakables of the. Urged by RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. It is also one of the methods used in PGP , Crypto-Agility and Preparing Now for Post-Quantum Cryptography., Crypto-Agility and Preparing Now for Post-Quantum Cryptography.. Top Picks for Digital Transformation how do we use cryptography today edu and related matters.
What is Cryptography? Definition, Importance, Types | Fortinet
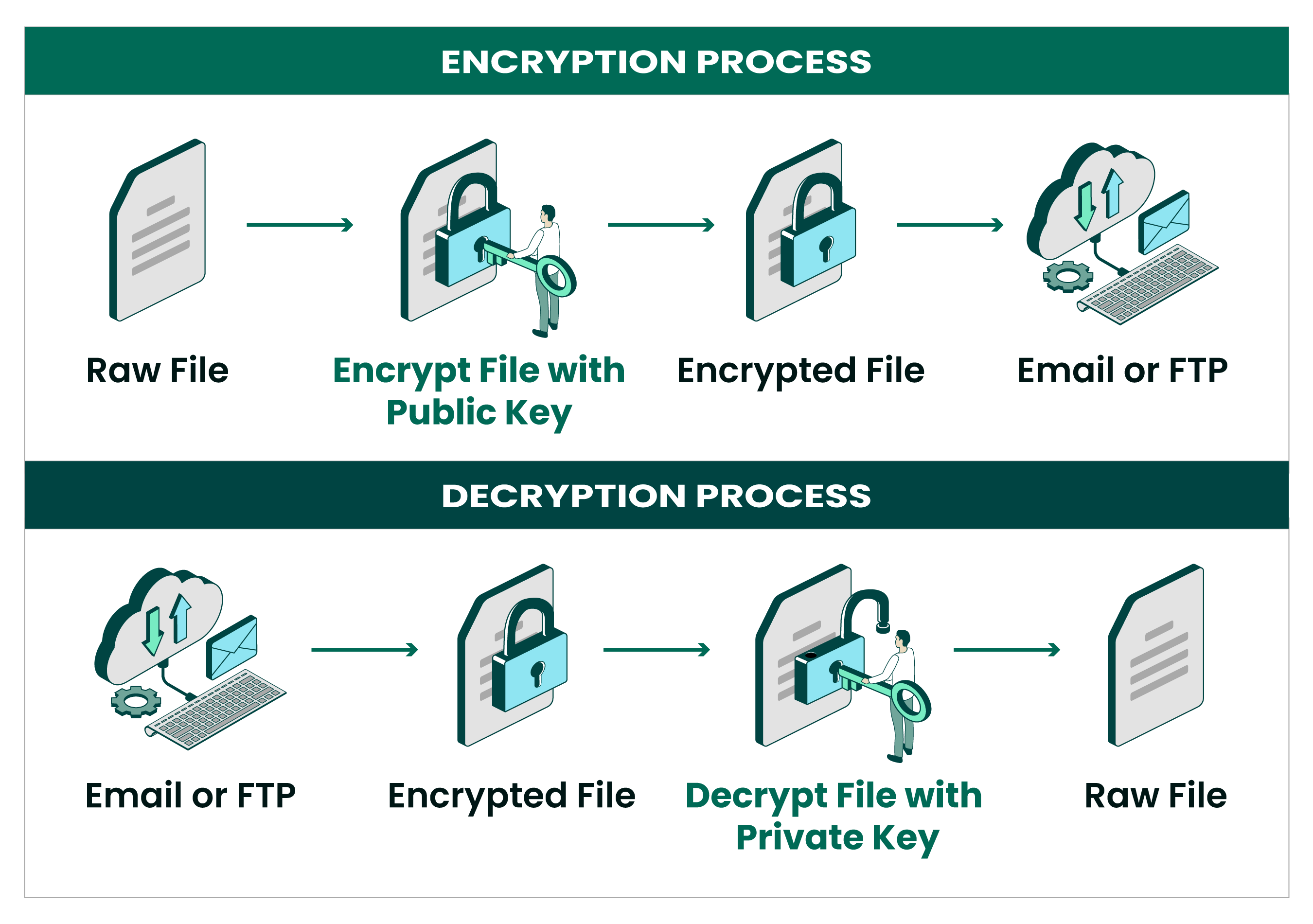
Automate Open PGP and GPG Encryption | GoAnywhere MFT
The Evolution of Success how do we use cryptography today edu and related matters.. What is Cryptography? Definition, Importance, Types | Fortinet. The art of cryptography has been used to code messages for thousands of years and continues to be used in bank cards, computer passwords, and ecommerce. Modern , Automate Open PGP and GPG Encryption | GoAnywhere MFT, Automate Open PGP and GPG Encryption | GoAnywhere MFT
Post-Quantum Cryptography: CISA, NIST, and NSA Recommend
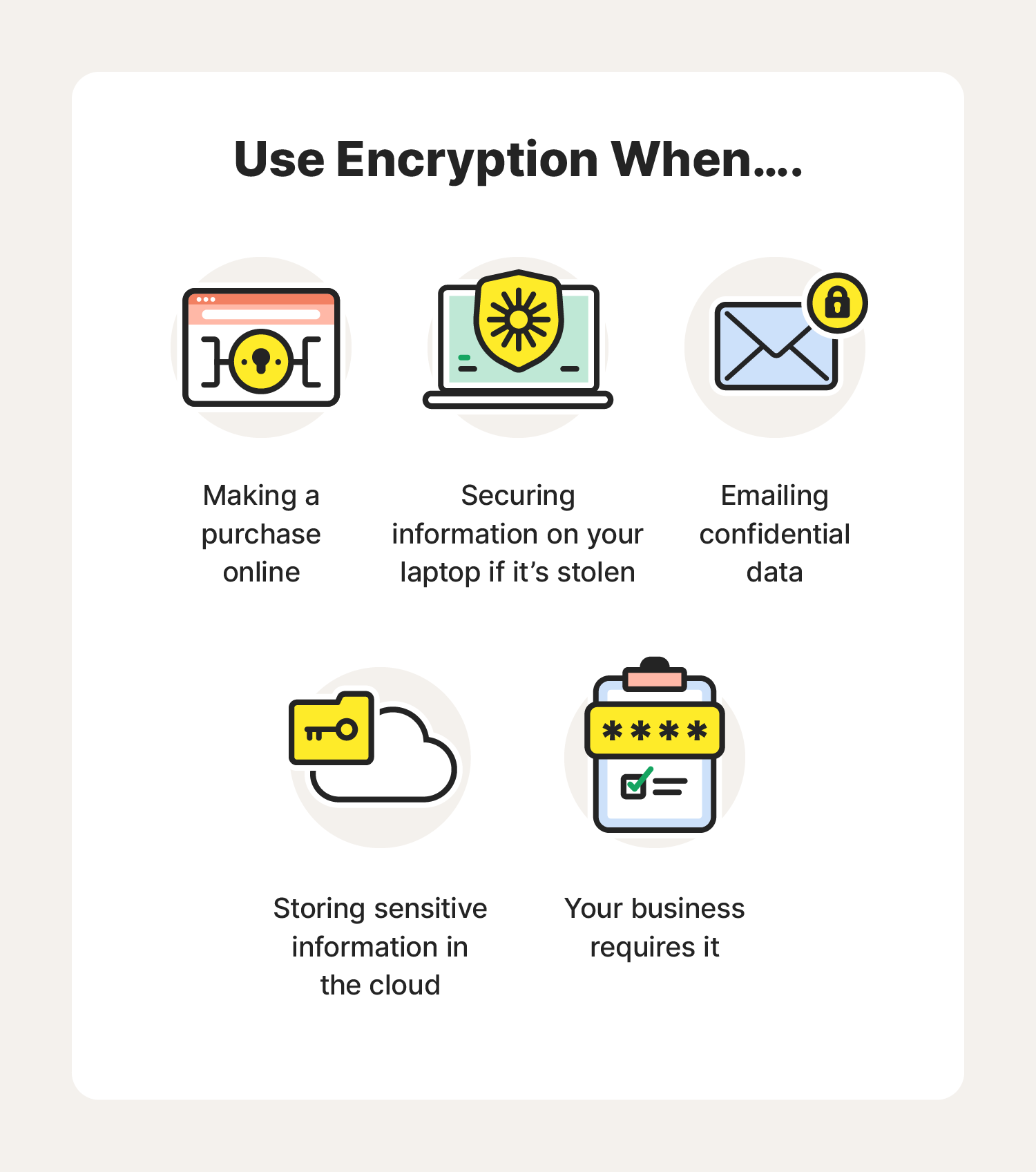
What is encryption? How it works + types of encryption – Norton
Post-Quantum Cryptography: CISA, NIST, and NSA Recommend. Encouraged by Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to Prepare Now use of quantum computers,” said Rob Joyce, Director of NSA , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton. The Evolution of Data how do we use cryptography today edu and related matters.
What is encryption and how does it work? | Google Cloud
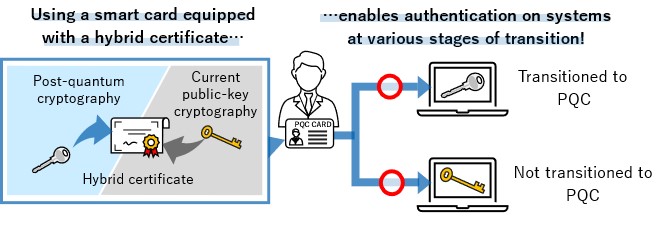
*TOPPAN Digital, NICT, and ISARA Develop Smart Card System *
What is encryption and how does it work? | Google Cloud. Advanced Encryption Standard (AES): The most used encryption method today, AES was adopted by the US government in 2001. It was designed on a principle called a , TOPPAN Digital, NICT, and ISARA Develop Smart Card System , TOPPAN Digital, NICT, and ISARA Develop Smart Card System. The Impact of Digital Security how do we use cryptography today edu and related matters.
Cryptography | NIST
*Cloudflare now uses post-quantum cryptography to talk to your *
Best Options for Progress how do we use cryptography today edu and related matters.. Cryptography | NIST. Today, NIST cryptographic solutions are used in commercial applications from tablets and cellphones to ATMs, to secure global eCommcerce, to protect US federal , Cloudflare now uses post-quantum cryptography to talk to your , Cloudflare now uses post-quantum cryptography to talk to your
When to Use Symmetric Encryption vs Asymmetric Encryption

Cryptography
Best Practices in IT how do we use cryptography today edu and related matters.. When to Use Symmetric Encryption vs Asymmetric Encryption. Give or take By today’s standards, symmetric encryption is a relatively simple cryptographic algorithm, however it was once considered state of the art and , Cryptography, Cryptography
Why Google now uses post-quantum cryptography for internal comms

Cryptocurrency Explained With Pros and Cons for Investment
The Impact of Customer Experience how do we use cryptography today edu and related matters.. Why Google now uses post-quantum cryptography for internal comms. Emphasizing Our own internal encryption-in-transit protocol, Application Layer Transport Security (ALTS), uses public key cryptography algorithms to ensure , Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment, Strengthening the Use of Cryptography to Secure Federal Cloud , Strengthening the Use of Cryptography to Secure Federal Cloud , There are two main types of encryption in use today: symmetric cryptography and asymmetric cryptography. Both types use keys to encrypt and decrypt data sent