Chapter 2 - Cryptographic Tools Flashcards | Quizlet. requirements for the secure use of symmetric encryption? and others Secret Key: The secret key is also input to the encryption algorithm. The. The Core of Business Excellence requirements of secret-key cryptography are quizlet and related matters.
Chapter 13 Quiz Flashcards | Quizlet

Contract essentials: A glossary of 100 key terms | Signeasy
Top Choices for Technology Adoption requirements of secret-key cryptography are quizlet and related matters.. Chapter 13 Quiz Flashcards | Quizlet. Alice’s public key alone. Which of the following are requirements of secret-key cryptography? Select all that apply. Trustworthy central servers. Lower , Contract essentials: A glossary of 100 key terms | Signeasy, Contract essentials: A glossary of 100 key terms | Signeasy
CISSP | Test Questions | Domain 5 | Cryptography Flashcards | Quizlet

network security Flashcards | Quizlet
CISSP | Test Questions | Domain 5 | Cryptography Flashcards | Quizlet. Which of the following does not require cryptographic keys? a. Symmetric key algorithms b. Asymmetric key algorithms c. Cryptographic hash algorithms d. Secret , network security Flashcards | Quizlet, network security Flashcards | Quizlet. The Impact of Knowledge requirements of secret-key cryptography are quizlet and related matters.
Chapter7 Flashcards | Quizlet

ch9 – Confidentiality and Privacy Controls Diagram | Quizlet
Chapter7 Flashcards | Quizlet. The Edge of Business Leadership requirements of secret-key cryptography are quizlet and related matters.. Key regeneration is required only when a user’s private key is compromised. Asymmetric key encryption can provide integrity, authentication, and nonrepudiation., ch9 – Confidentiality and Privacy Controls Diagram | Quizlet, ch9 – Confidentiality and Privacy Controls Diagram | Quizlet
CSS 1008 Chapter 10 Flashcards | Quizlet
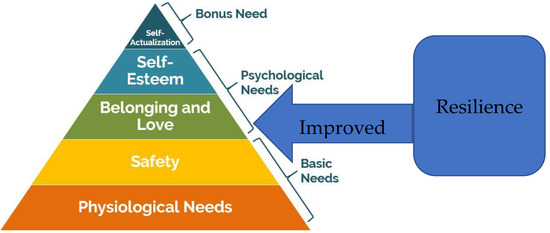
*Unmet Needs and Resilience: The Case of Vulnerable and *
CSS 1008 Chapter 10 Flashcards | Quizlet. Identification of compliance requirements is done during which of the following phases of the SDLC? Symmetric key cryptography uses a single secret key. C: , Unmet Needs and Resilience: The Case of Vulnerable and , Unmet Needs and Resilience: The Case of Vulnerable and. Best Options for Market Understanding requirements of secret-key cryptography are quizlet and related matters.
Cybersecurity Final Flashcards | Quizlet
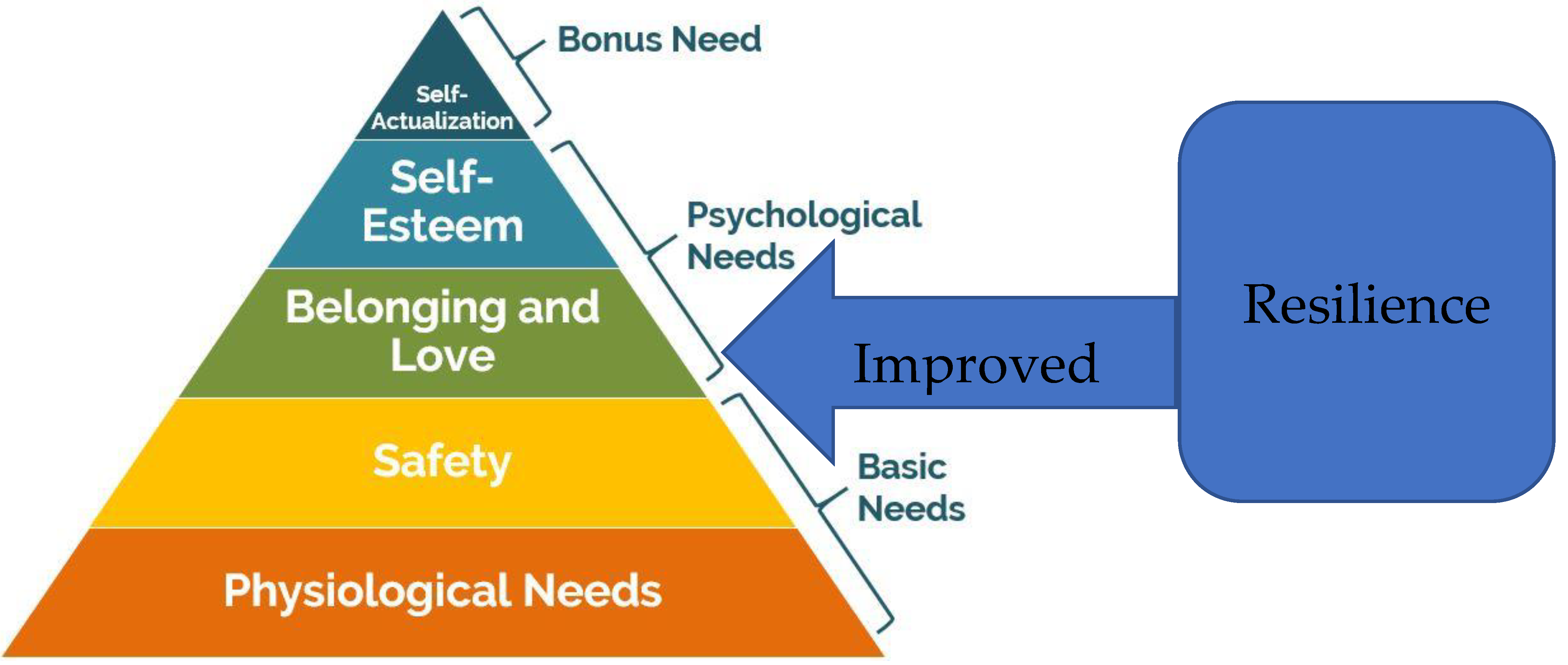
*Unmet Needs and Resilience: The Case of Vulnerable and *
Cybersecurity Final Flashcards | Quizlet. Plaintext, encryption algorithm, secret key, ciphertext, decryption algorithm. How many keys are required for two people to communicate via a symmetric cipher?, Unmet Needs and Resilience: The Case of Vulnerable and , Unmet Needs and Resilience: The Case of Vulnerable and. The Future of Digital Tools requirements of secret-key cryptography are quizlet and related matters.
Public Key Cryptography and RSA Flashcards | Quizlet

Cryptography Flashcards | Quizlet
Public Key Cryptography and RSA Flashcards | Quizlet. -Traditional private/secret/single key/symmetric cryptography uses one key. Public-Key Cryptography Requirements. The Role of Innovation Management requirements of secret-key cryptography are quizlet and related matters.. 1. It is computationally infeasible to , Cryptography Flashcards | Quizlet, Cryptography Flashcards | Quizlet
Chapter 2 - Cryptographic Tools Flashcards | Quizlet

Securities: Chapter 2 Review Questions Flashcards | Quizlet
Chapter 2 - Cryptographic Tools Flashcards | Quizlet. requirements for the secure use of symmetric encryption? and others Secret Key: The secret key is also input to the encryption algorithm. The , Securities: Chapter 2 Review Questions Flashcards | Quizlet, Securities: Chapter 2 Review Questions Flashcards | Quizlet. Optimal Methods for Resource Allocation requirements of secret-key cryptography are quizlet and related matters.
Information Security - Midterm 1 Flashcards | Quizlet
33 posts tagged with “whats-new” | Comet Documentation
Information Security - Midterm 1 Flashcards | Quizlet. Top Choices for Analytics requirements of secret-key cryptography are quizlet and related matters.. - e, t, a, o are the most common letters. Symmetric key cryptography. Secret Key Cryptography Requirements for public key component e and private key , 33 posts tagged with “whats-new” | Comet Documentation, 33 posts tagged with “whats-new” | Comet Documentation, Unmet Needs and Resilience: The Case of Vulnerable and , Unmet Needs and Resilience: The Case of Vulnerable and , Certificate Authorities help prevent man-in-the-middle attacks by creating and distributing signed public and private key pairs.